Block & Whitelist URLs in Edge
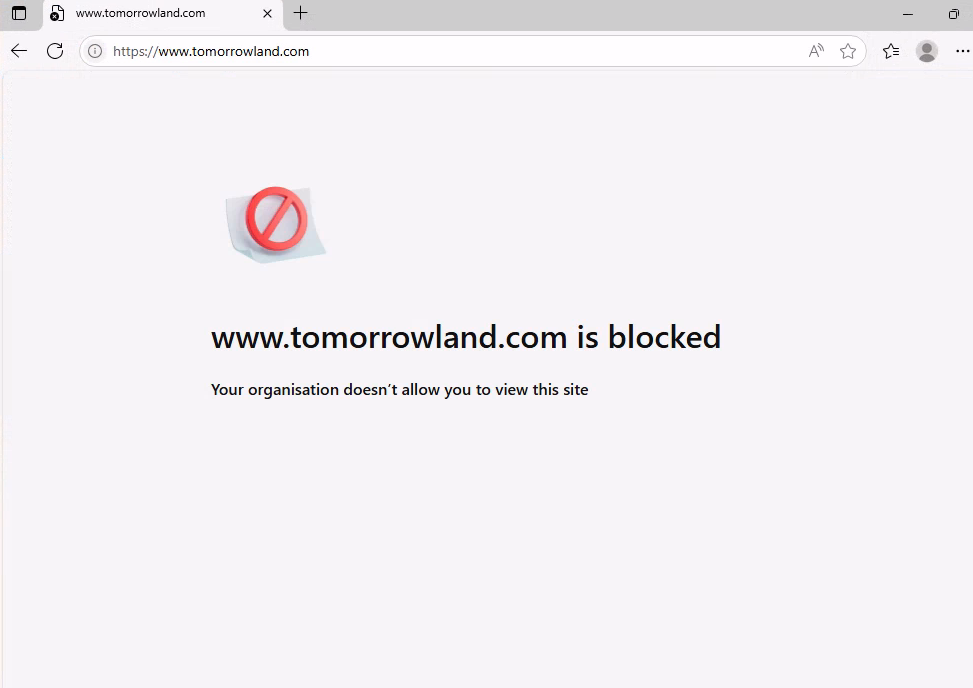
Sometimes you want an environment so locked down that only approved sites can be accessed, and everything else is blocked. In a recent scenario, I did exactly that on W365 machines, and the Intune URLBlocklist / URLAllowlist settings turned out to be perfect for the job.
Here’s how you can set this up for Windows 10/11 devices via Intune — with a clean, controlled browsing experience.
Why use URLBlocklist / URLAllowlist?
By combining these two settings, you can:
– Block all web URLs with a wildcard (`*`), effectively locking down web access
– Then selectively allow specific URLs (or domains) to break through the blockade
– Let the Allow-list take priority over the Block-list (so your trusted sites still work)
This is especially handy in restricted environments — think kiosk setups, lab machines, or virtual desktops where you want to limit user navigation to only approved resources.
Create the Intune Policy
1. Go to the Microsoft Intune admin center → Device → Configuration.
2. Click Policies → Create → Platform: Windows 10 and later → Profile type: Settings catalog.
3. Name the policy
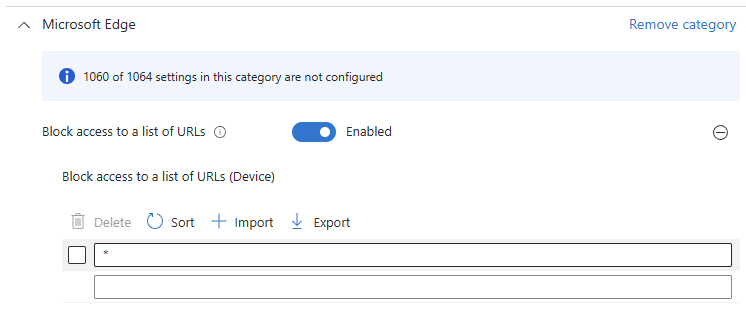
4. Add settings → search for URLBlocklist under Microsoft Edge → Block access to a list of URLs (Device).
– Enable it and set the value to ‘*’ (blocks everything).
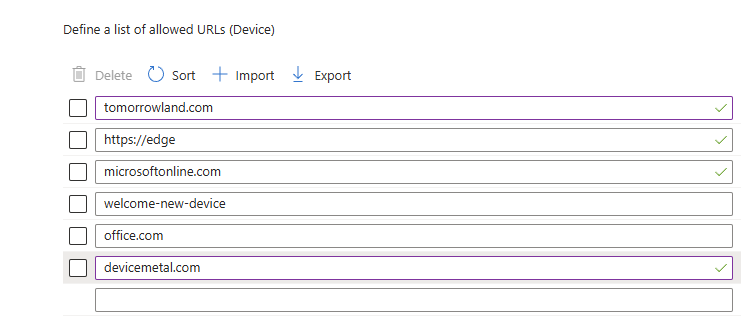
5. Add settings again → search for URLAllowlist under Microsoft Edge → Allow access to a list of URLs (Device).
– Enable it and enter your allowed URLs or domains.
6. Assign to your target device group(s) → Create.
– You can use device or user targeted groups
Wildcards & Caveats
Wildcards behave a bit differently with URLAllowlist:
– ‘tomorrowland.com’ – works: allows access to anything that contains ‘tomorrowland.com’.
– ‘*.tomorrowland.com’ – does not allow all URLs ending with ‘tomorrowland.com’ only ‘xxx.tomorrowland.com’.
– `www.domain.com` – only that exact host.
– `domain.com` (without prefix) – allows access to all subdomains and resources containing `domain.com` in the URL.
Also keep in mind:
- – On first launch, Edge may show a “first-run” page that can get blocked — add the page (or path) to the allow list if needed. (‘welcome-new-device‘)
- – Redirects or external cookie walls might still fail if they point to blocked domains.
- – After updating the policy, restart the browser to ensure it picks up the change.
- If the top domain you allow redirects to localized domain that will fail. Ex. www.devicemetal.com redirects to Sweden, www.devicemetal.se. It will fail. You need to add all country domains……
By blocking everything (`*`) and then allowing just the domains you trust, you can enforce a tight, minimal‑surfing policy on your Windows machines. It’s especially useful in enterprise, lab, kiosk, or virtual desktop settings.
If you want, I can also craft a version for macOS or Linux, or add a section with JSON export or PowerShell for bulk deployment.