Compliance failure with Pluton TPM
During and enrolment of a customer we experienced a strange thing. On our Lenovo devices with AMD cpu we couldn’t get them compliant in Intune. The device itself was all good, TPM enabled, Bitlocker working and so on. This turned out to be an issue with the Microsoft Pluton security processor and reporting compliance with Intune. It is an known issue but I do not know the status or haven’t found any official solution for it. But it can be solved.
I am not going into how, what and why about the Microsoft Pluton but you can read more here:
Microsoft Pluton security processor – Windows Security | Microsoft Learn
The issue
We cannot get the device compliant because of the failure to report bitlocker, code integrity and secure boot.
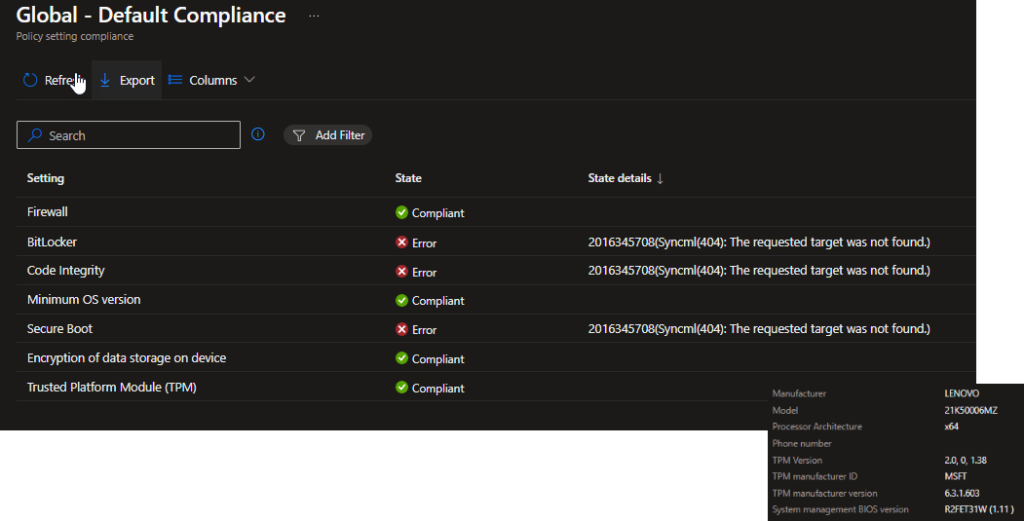
Solution
The easiest way is to disable the Pluton and just reinstall the device but there is a way to do it without reinstalling and it will keep the users profile.
Create local admin account on the device. This is needed since the trust to Entra is going to be broken and Entra ID accounts nor LAPS will work.
Run the following commands in an elevated command prompt:
net user tempadmin password123 /add
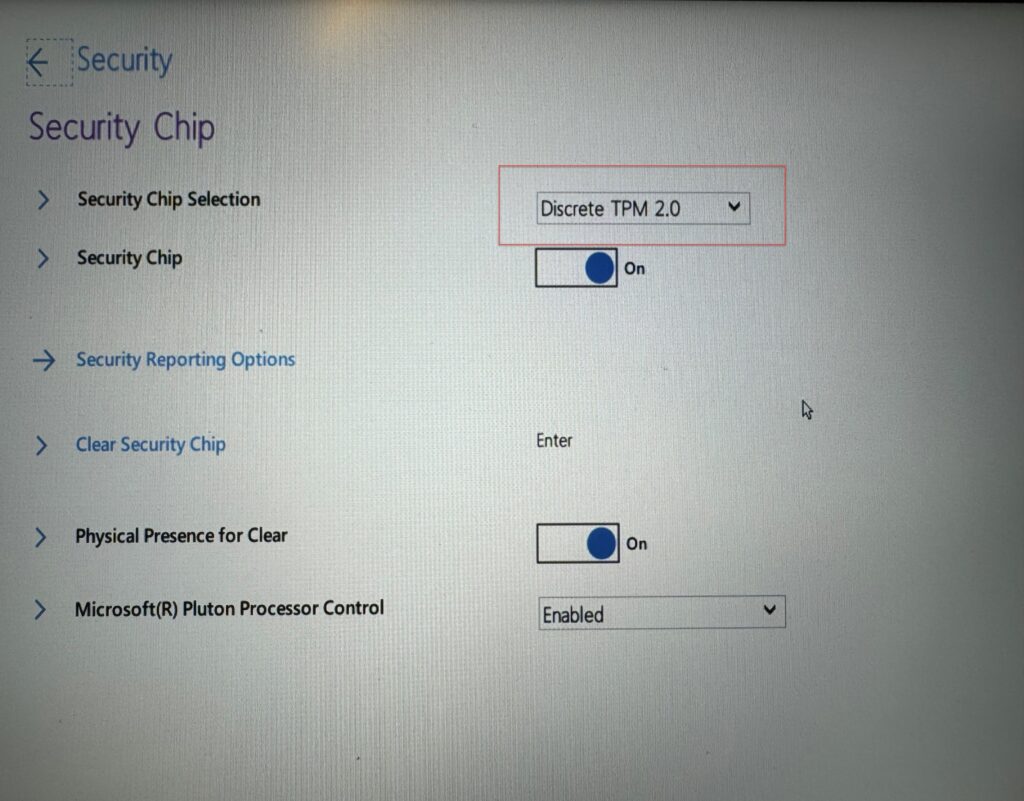
Net localgroup administrators tempadmin /addOnce this is done reboot the device into BIOS settings. Change the TPM type to Discrete and save/exit.
This is from a Lenovo device:
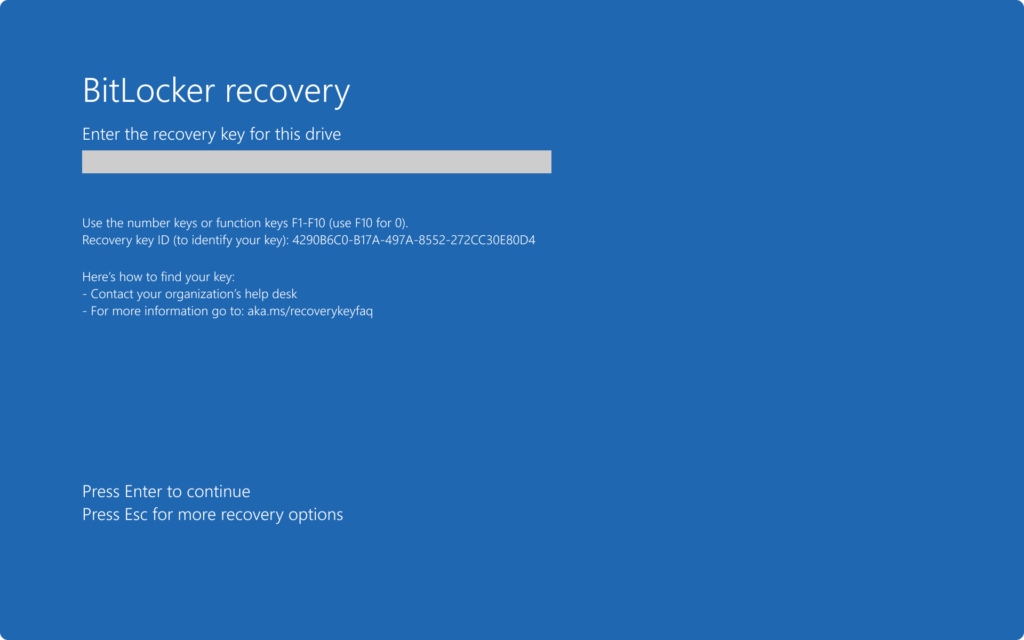
The device will now boot into Bitlocker recovery, get it from Entra or Intune portal and start up the device.
Now logon with the local admin account that was created in the first step. Run the following command to make the device released from Entra Id. Make sure you have Internet connectivity.
Dsregcmd /leaveOnce that is done, delete the object from Intune. And do another reboot of the device this time it should not ask for the recovery keys. Logon with the local admin account again.
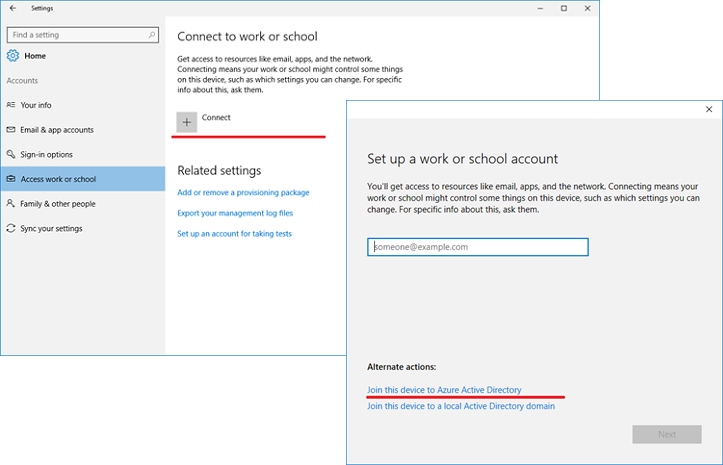
Now we are going to add it to Intune once again but via the settings in Windows. go tO Settings and ‘Access to work and school”. Make sure that there is no accounts configured. In that case just remove them. Then click connect and under alternate action choose “Join the device to active directory”.
Let the user login with their Entra ID.
Missing screenshot…..
Now we can remove the temporary admin account and do another reboot.
Once rebooted the user can logon as usual and the Windows hello guide will trigger if that is enabled.
The bitlocker encryption is started and might take a while for it to complete. give it an hour and the device should be good to go and compliant in Intune.
