Windows 11 and the SSO popup. DMA to blame.
Deploying a brand new installation with autopilot can be really automated. User login and they can start work but, they need to comply to use SSO for apps. It’s annoying when we have set the base for the user and do not want any blockers for apps or extra popups for the users.
Why Are These Settings in Windows 11?
Microsoft’s Response to the Digital Markets Act (DMA)
Microsoft has been working to ensure compliance with the Digital Markets Act (DMA) in the EEA. The DMA aims to prevent dominant tech companies from favoring their own services over competitors.
“As part of this ongoing commitment to provide your organization with solutions that comply with global regulations like the DMA, we will be changing the ways Windows works. Signing in to apps on Windows is one area where we will be making such changes.”
Since Microsoft is only obligated to comply with the Digital Markets Act, these changes will only be valid for users in the 27 regions part of the EEA. However, we can control these changes through a JSON file known as “IntegratedServicesRegionPolicySet.json” which is located in the “C:\Windows\System32\” folder, and change permissions the file and then modify the settings to apply the changes to any region.
For European users, this means:
- Microsoft must allow third-party identity providers (IdPs) like Okta and Google for authentication.
- Users should have more control over Edge/Bing search suggestions.
- Less forced integration of Microsoft services.
These changes are not applied automatically—IT admins must manually configure Windows 11 using the IntegratedServicesRegionPolicySet.json file.
What is the IntegratedServicesRegionPolicySet.json File?
Windows 11 includes a hidden JSON file in:
C:\Windows\System32\IntegratedServicesRegionPolicySet.json
This file allows Microsoft to control feature availability for users in the EEA. Key settings include:
- Third-party identity provider (IdP) authentication
- Bing and Edge search ad settings
- Web-based integrations in Windows Search
By editing this JSON file, organizations can disable unnecessary integrations and allow third-party SSO.
The list of features in IntegratedServicesRegionPolicySet.json
- Edge is uninstallable
- User can disable web search
- Narrator scripting extensions are enabled
- File Explorer Search is third party extensible
- First party File Explorer Search is allowed
- Featured apps show in Open With dialog
- Third party search providers show in search
- Third party search highlight content in search zero input
- First party search highlight content in search zero input
- Third parties can customize the Taskbar Gleam
- First party Taskbar Gleam customization is shown
- Search MRU shows third party provider
- Edge is required for web search
- System components are differentiated from apps
- Backup options are restricted
- Show files from the MS Office MRU redommendation provider
- Third party feed is shown in Widgets
- Third party Widgets are shown in Widgets feed
- First party Widget feed can be enabled
- Use default web protocol for Widget links
- Restrict widgets data sharing
- Restrict third-party widgets data sharing
- UTC events should be tagged restricted
- XBox performance fit data sharing
- Shared ODD consent
- Windows Copilot
- Automatic app sign-in
- Notifications on the taskbar for Widgets
- Show recent web searches in search zero input
- Show website items in start recommendations
- Widget sign-in is restricted to default account
- Widget third-party taskbar badges are enabled
- Widgets should be restricted to static recommendations
- First-party widgets have optimized frame and taskbar integration
Editing the JSON File to Enable Third-Party SSO and Remove Ads
To modify the file, we must:
1️⃣ Adjust file permissions to allow modifications.
2️⃣ Edit the JSON content to enable third-party authentication.
3️⃣ Deploy these changes via Intune.
Modify File Permissions with PowerShell
Before modifying the JSON file, we need to grant SYSTEM full control.
I usually set this in the Pre-Install part of PSADT.
## <Perform Pre-Installation tasks here>
Write-ADTLogEntry -Message 'Updating ACL for C:\Windows\System32\IntegratedServicesRegionPolicySet.json'
try {
$acl = Get-Acl 'C:\Windows\System32\IntegratedServicesRegionPolicySet.json'
$AccessRule = New-Object System.Security.AccessControl.FileSystemAccessRule("NT Instans\SYSTEM","FullControl","Allow")
$acl.SetAccessRule($AccessRule)
$acl | set-acl 'C:\Windows\System32\IntegratedServicesRegionPolicySet.json'
}
catch {
$errMsg = $_.Exception.Message
Write-ADTLogEntry -Message $errMsg
}
Editing the JSON File
Once permissions are updated, we can modify the JSON file to enable third-party authentication.
This is how I change the JSON:
Before change
{
"$comment": "Automatic app sign-in",
"guid": "{1d290cdb-499c-4d42-938a-9b8dceffe998}",
"defaultState": "enabled",
"conditions": {
"region": {
"disabled": ["AT", "BE", "BG", "CH", "CY", "CZ", "DE", "DK", "EE", "ES", "FI", "FR", "GF", "GP", "GR", "HR", "HU", "IE", "IS", "IT", "LI", "LT", "LU", "LV", "MT", "MQ", "NL", "NO", "PL", "PT", "RE", "RO", "SI", "SK", "YT"]
}
}
After change:
{
"$comment": "Automatic app sign-in",
"guid": "{1d290cdb-499c-4d42-938a-9b8dceffe998}",
"defaultState": "enabled",
"conditions": {
"region": {
"disabled": []
}
}
This setting removes the Microsoft Account requirement for authentication, allowing third-party IdPs to function properly.
Deploying the Configuration with Intune & PSADT
The easiest way to push this change is to use PSAppDeployToolkit. We can make sure the permisisons is changed and the file copied.
Prepare the Deployment Package
Save the modified IntegratedServicesRegionPolicySet.json file. in the Files folder of te PSADT. I also put the original file there along with a check file. The last one is just to have as a detection method.
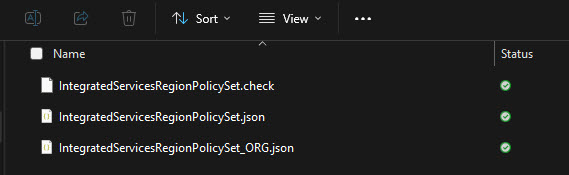
This is how the file copy is done:
## <Perform Installation tasks here>
Copy-ADTFile -Path "$($adtSession.DirFiles)\IntegratedServicesRegionPolicySet.json" -Destination "C:\Windows\System32\IntegratedServicesRegionPolicySet.json"
Copy-ADTFile -Path "$($adtSession.DirFiles)\IntegratedServicesRegionPolicySet.check" -Destination "C:\Windows\System32\IntegratedServicesRegionPolicySet.check"
Create a Win32 App in Intune
- Use
IntuneWinAppUtil.exeto package the script and JSON file into a.intunewinfile. - Upload the package to Intune:
- Intune Admin Center → Apps → Windows → Add
- Select Win32 app, then upload the
.intunewinfile.
Configure the Installation
- Install command:
Deploy-Application.exe -DeploymentType Install - Detection script: Check that the IntegratedServicesRegionPolicySet.check is there.
Step 4: Assign to Devices
- Target the correct device groups.
After a reboot this behaviour is gone. Works well to push this during autopilot!